Misuse of Computing Technology
As is the case with most types of technology, computing resources can be misused in many different ways. Protecting technology from being wielded to cause harm is a difficult but important task. However, there are ways to minimize the risk of misuse and keep technology safer. Misuse
With vast amounts of information stored in computer databases, it is all too possible for attackers to obtain and change sensitive data. Successful hackers can commit identity theft, or sell the information that they steal to other cybercriminals. Another way computing resources can be misused is the creation of malware, malicious software that can hijack and harm computers. With malware, attackers are able to steal data and damage entire systems. Protection
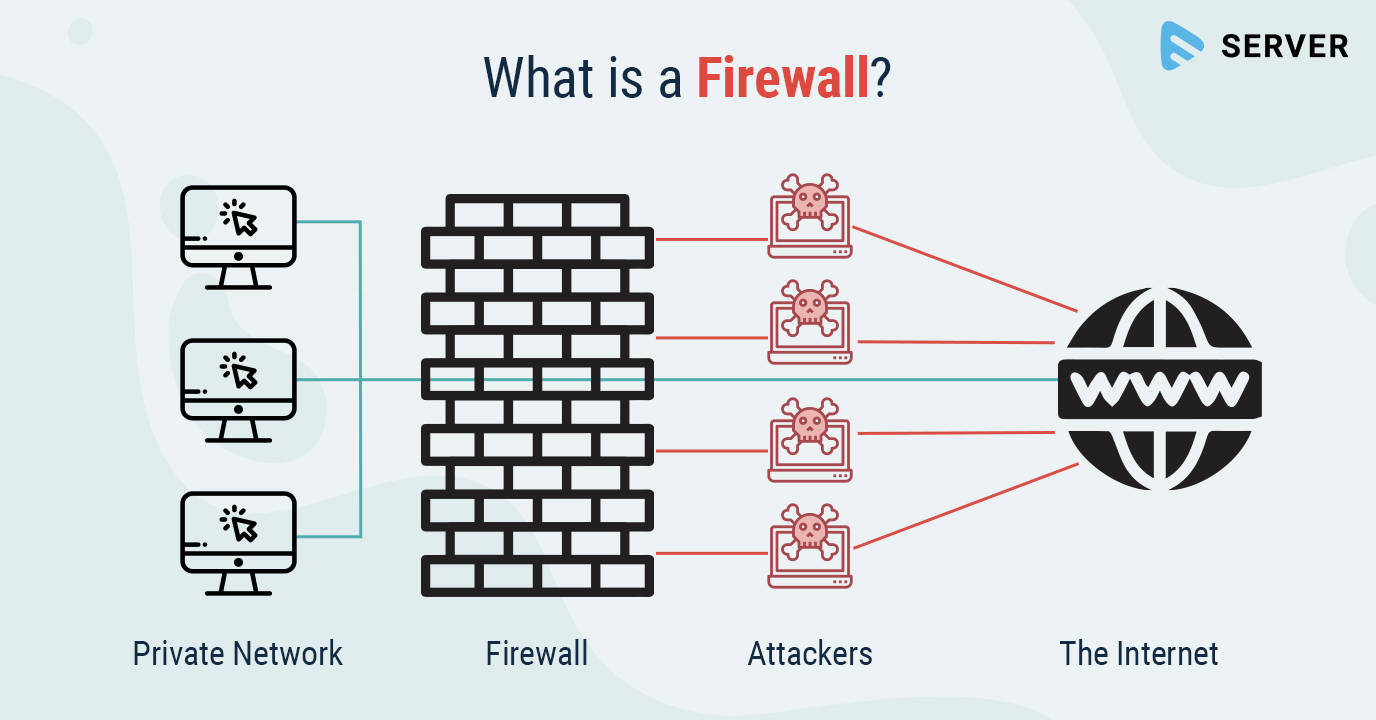
Strong cybersecurity measures allow for computer systems that are less susceptible to attacks. On an individual level, designing unique passwords can help safeguard accounts and devices from potential hackers. Antivirus programs detect malware and are also a strong source of protection. Larger systems usually utilize a number of security measures as well, such as requiring multi-factor authentication from users, encrypting data, and monitoring networks via firewalls.